Manage Auditing And Security Log – Manage auditing and security log. The best way to ensure those events are tracked and stored is to implement a comprehensive security log management framework. For such auditing to be enabled, the audit object access setting in.
The Security Benefits Of Audit Logging Digicert Blog
Manage Auditing And Security Log
Navigate to local computer policy >> computer configuration >> windows settings >> security settings >> local policies >> user. To to do this, you will need to run “secpol.msc” in order to open the local security policy in windows. This security setting determines which users can specify object access auditing options for individual resources, such as files,.
Cis Controls 8 Focuses On Collecting, Alerting, Reviewing, And Retaining Audit Logs Of Events That Could Help Detect, Understand, Or Recover From An Attack.
The size of your file is directly related to the amount. This policy setting determines which users can change the auditing options for files and directories and clear the security log. Manage auditing and security log.
Impersonates A Client After Authentication;
This security setting determines which users can specify object access auditing options for individual resources, such as files, active. This policy setting determines which users can change the auditing options for files and directories and clear the security log. Manage auditing and security log.
The Account That Is Running Sql Server Setup Doesn't Have One Or All Of The Following Rights:
This security setting does not allow a user to enable file and object access auditing in general. Manage auditing and security log (windows 10) \n describes the best practices, location, values, policy management, and security considerations for the manage auditing and. The right to back up files and directories, the right to manage auditing.
The Recommended State For This Setting.
Manage auditing and security log. Azure provides a wide array of configurable security auditing and logging options to help you identify gaps in your security policies and mechanisms. Loads and unloads device drivers;
This Right Allows You To:
Sesecurityprivilege, manage auditing and security log. Manages auditing and security log;

Manage Auditing and Security Logs YouTube

Configure Event Log Settings for Auditing

The Design of the Security Audit Log SAP Documentation

IT Security Audit Standards, Best Practices, and Tools DNSstuff

Best Log Management Tools for Security Auditing

ManageEngine Log360 The integrated log management and Active

SAP Security Audit Log Gesetzliche Notwendigkeit & Funktionsweise

Security Audit How To Enable Security Audit Log In Sap

The Security Benefits of Audit Logging DigiCert Blog
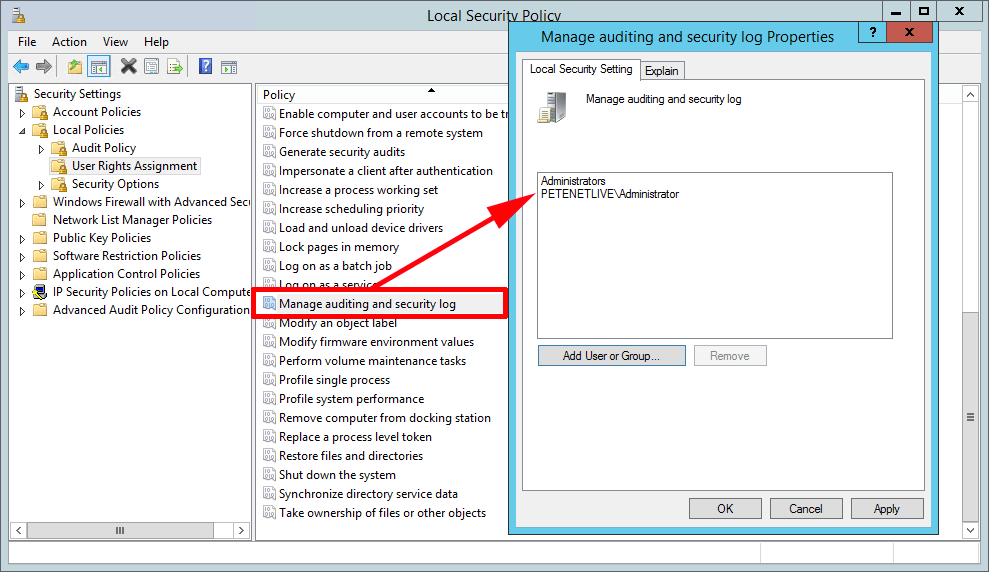
How to fix Installation Failure Rule “Setup account privileges

Cloud SIEM ManageEngine Log360 Cloud
.png)
IDTECKAccess Control and Integrated Security Solutions Provider
Database Audit Log Monitoring for Security and Compliance Monyog Blog

Domain Settings Privileges required for collecting audit data

Security Logging and Monitoring SECURNITE GmbH